The Heroic Blog
IT and Cybersecurity Tips
How Technology Is Shaping the Future of Legal Practices
The legal profession, often deeply rooted in tradition, is no stranger to innovation. From digital case management to advanced cybersecurity, technology is transforming how law firms operate. Managing complex tasks and safeguarding sensitive data can be overwhelming for legal professionals—but with the right tech solutions, navigating the digital age is...
Cybersecurity Isn’t Just for Techies Anymore—Why Technology Legislation Matters More Than Ever for Business Leaders
The Threats Have Changed—and So Must We If you’re running a business today, odds are you’ve got a hundred things on your plate—growth, operations, financials, people. I get it. I’ve been there too. But there’s one more thing that’s quietly becoming just as critical as any of those: cybersecurity. Or...
Embarking on Your Secure AI Journey: How Businesses Can Leverage AI Safely
Artificial intelligence (AI) is often hailed as the next frontier of innovation, transforming business operations and delivering unprecedented efficiencies. With capabilities doubling every 70 days, AI’s march forward has never been more relentless—or more exciting. Yet for many C-Suite execs, owners, and business technology managers, the real question isn’t whether...
Future-Proof Your Business: Why IT Infrastructure Is the Backbone of Tech Growth
Learn about IT infrastructure's vital role in tech businesses, including key components and best practices for optimal performance and growth.
Why Silicon Valley Businesses Need Proactive IT Management Now
Learn why proactive IT management is crucial for Silicon Valley businesses, including strategies for operational efficiency and risk management.
Why Portland Managed Services Are More Cost Efficient Than Break-Fix IT
Understand cost implications, benefits, and transition strategies for businesses seeking efficient IT solutions and Portland managed services.
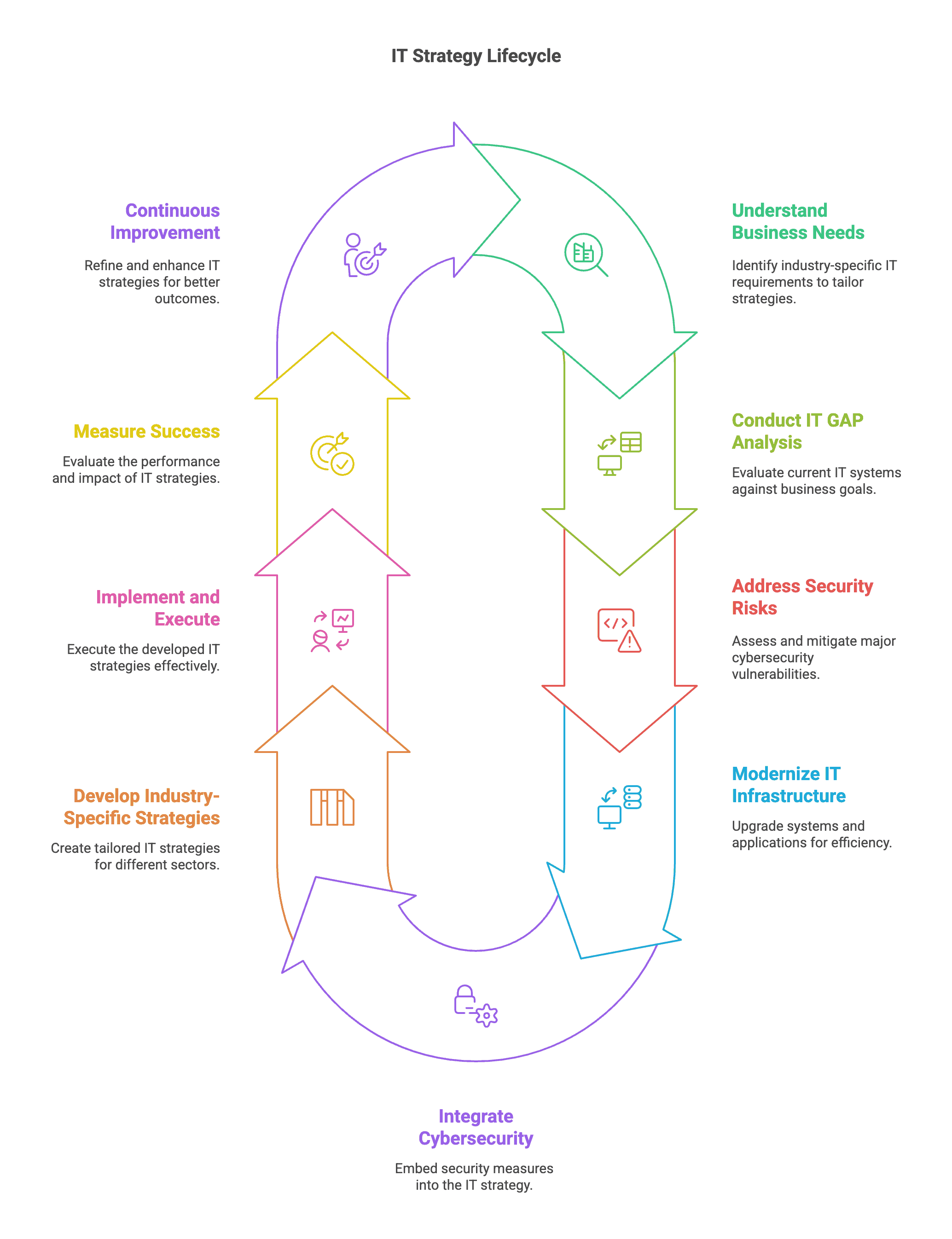
Custom IT Strategy for Portland Businesses: Manufacturers & Professional Services
In today’s digital-first business environment, having the right technology isn’t just an advantage—it’s essential for survival. Portland businesses face unique challenges that require tailored technology solutions, not one-size-fits-all approaches. Whether you’re a manufacturing plant on the industrial eastside or a law firm downtown in Pioneer Square, your IT strategy must...
Challenges Businesses Will Face With Their Portland IT Systems in 2025
Learn how small businesses can tackle critical IT challenges in 2025, from cybersecurity threats to remote work infrastructure and budget constraints.
Ensuring Portland HIPAA Compliance: Law Firm Checklist
Learn essential Portland HIPAA compliance requirements for law firms, including privacy rules, security measures, and best practices for protecting PHI.
Ensuring San Jose Business Compliance with PCI DSS
Explore strategies to ensure San Jose business compliance with PCI DSS. Learn how to protect sensitive data and implement San Jose cybersecurity measures.

Download the
Business Owner’s Guide to Cybersecurity
Browse Topics
Protect & Streamline Your Firm
Contact us today to discover how our team of IT heroes can help secure, streamline, and optimize your business so you can focus on growth while we handle your tech.